Keywords
Description
Today’s cybersecurity relies heavily on cryptography that offers a set of mathematically based methods for delivering essential security services. These include:
- Confidentiality: limiting who has access to data.
- Data integrity: ensuring that any unauthorized modifications to data are discovered.
- Authentication: identifying the correct source of data.
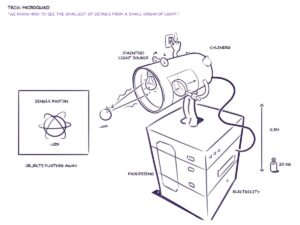
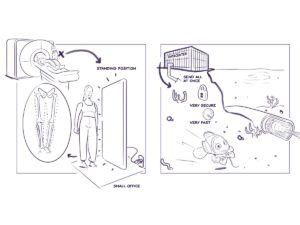
In general, we apply the concept of QKD, by using satellites to distribute quantum keys to the end users, which each will use our single quantum detector to detect the key sent from satellites. Therefore, since the process is end-to-end users, there is no third party involved, meaning there is less chance the key will be leaked. In addition, since we are using a light signal, if any third party tries to eavesdrop on the information in the midway, they will have to measure the system.